Earlier I described the Plausibly Deniable DataBase (PDDB). It’s a filesystem (like FAT or ext4), combined with plausibly deniable full disk encryption (similar to LUKS or VeraCrypt) in a “batteries included” fashion. Plausible deniability aims to make it difficult to prove “beyond a reasonable doubt” that additional secrets exist on the disk, even in the face of forensic evidence.
Since then, I’ve implemented, deployed, and documented the PDDB. Perhaps of most interest for the general reader is the extensive documentation now available in the Xous Book. Here you can find discussions about the core data structures, key derivations, native & std APIs, testing, backups, and issues affecting security and deniability.
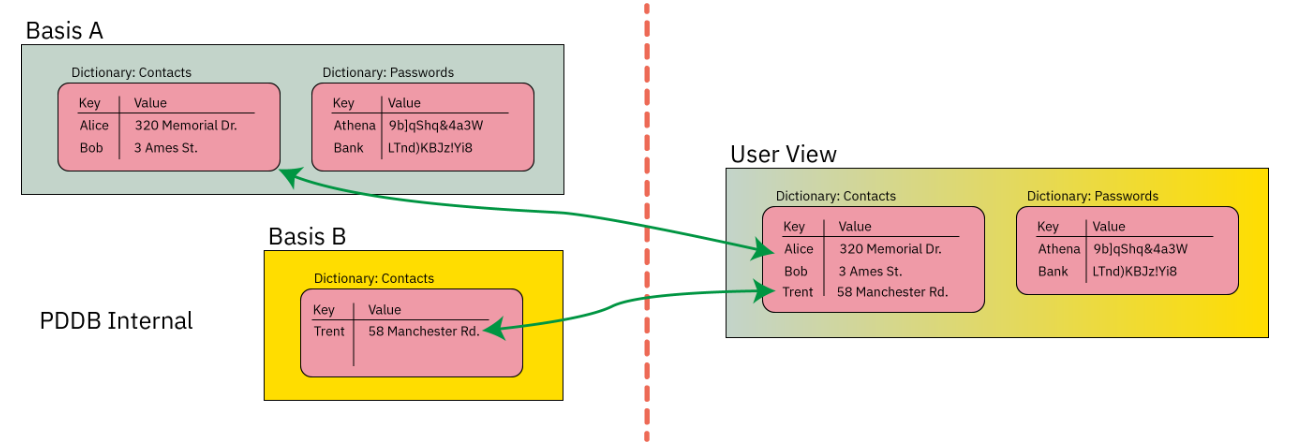
Very nice.
Until you use the PDDB in any real world application.
Then you leak undeniable proof of data existence all over (logs, connections, caches, links, bookmarks).
And then comes rubber-hose cryptanalysis.
That’s called PIR Private Information Retrieval and pretty well studied in Cryptography.