There is a WSJ article that was printed today that reports on some of my (relatively insignificant) dabblings on the Xbox360. I have kept a very low profile with respect to working on the Xbox360, but I guess this article changes things. The article is reasonably accurate, but I feel the need to clarify a few things.
First, hacking the 360 is not a race between me and The Specialist; the “bunnie v. Specialist” tag line is a result of the WSJ’s editorial latitude and their perspective on the scene (and I, of all people, must respect their first amendment rights to report as they see fit, seeing as how I also stand behind the first amendment to protect my right to blog about controversial hacking topics). I give The Specialist huge props for his DVD firmware hack; it’s a great hack and I respect his work a lot. When we found out about his work we were very excited and appreciated the great contributions he’s made in furthering an understanding of the overall security system of the 360. We wouldn’t be anywhere near where we are today without the openness and information-sharing that pervades the hacking scene, and I hope that the portrayal of hacking as a competitive sport does not close off these avenues. I know that I would not be where I am today if it were not for the great collaborations I’ve had in the past with so many anonymous hackers, and my ability to contribute on the 360 would also be greatly diminished if I were to lose such valuable collaborations.
Second, while I have been dabbling in the Xbox360, I’ve been a bit delinquent lately–very busy with my day job, and I haven’t touched the Xbox360 to do any real work on it for a couple months. I owe Speedy22 an apology for not being more diligent about sending him micrographs of the XCPU, but really, right now the pictures aren’t very interesting because all the metal is still on the chip (working with a local vendor to get it removed but it takes a lot of time). Speedy22 was kind enough to provide me some samples of the Xbox360’s chips to digest, and I appreciate his generosity in sending them to me. I also owe tmbinc an apology, I was supposed to run a set of experiments on the “virgin” ROM images that I never got around to. If you still need those results, I’ll get to it.
In the meantime, I hope to refine a technique that will gain access to the polysilicon layer of the XCPU while being non-destructive to the function of the chip. Such access is currently thought to be a major stumbling block to extracting the necessary keys for decrypting firmware images on the Xbox360–and the first step toward homebrewing code on the Xbox360. I wouldn’t hold my breath, however–the technique is very risky and I don’t have a whole lot of time to perfect it. I have to build some custom equipment to help control the etch bath properties for peeling back the silicon. Still, it will be fun and even if it is not successful, I’ll learn something new while I develop the hack!
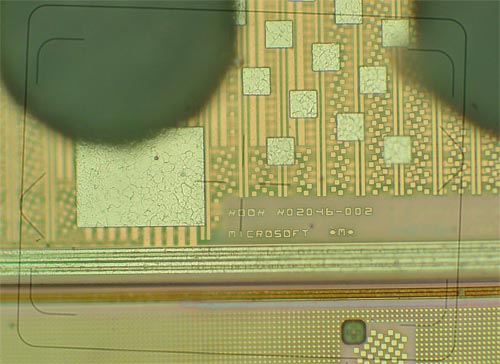
(above) Micrograph of the logo region on the 360 XCPU die. The pattern of metal dots you see are the fill pattern used to make the metal layers statistically uniform at the macro-level for the purposes of chemical-mechanical polishing (CMP), a process used to planarize metal layers during manufacturing. CMP is an important enabling technology for both copper technology (dual-damascene processing) as well as for enabling very high metal-layer counts to meet the wiring demands of today’s technology. Before CMP technology, metal layers would develop a 3-D topography that would limit the height of metal stacks. As one can see, CMP tiles also make a great tamper-resistance measure because the CMP tiles interfere with reading the underlying silicon patterns. Peeling back these layers is a destructive process, and can be a difficult and time-consuming. It requires a similar chemical-etch and mechanical-polish technique used during fabrication, and the technique has to be precise to sub-micron depths across a relatively large area. Alternative techniques are being developed to solve this problem.
As a silicon tourist myself (I’ve been prying the lids off ceramic PGA’s for years) I’m really curious about how you get at the silicon these days. As I understand it, the main chips of the XBox 360 are flip chips – soldered face down and then glued in place with hi-tech epoxies. How do you even get the die loose from its mounting substrate without demolishing it? Sneaking past the upper metal layers with the chip still functioning is even more amazing.
(My favorite lid to pop off – the Original Pentium (P60). Beautiful large gold die.)
I am wondering if the metal layers can be chemically remove once it is exposed by polishing.
Since it is metallic copper, would the usual PCB etchant (eg. Ammonium persulphate) works?
Or can it be removed with a electroplating process? (see picture in URL)
http://en.wikipedia.org/wiki/Electroplating
If the chip substrate connected to +ve terminal, would the leakage current of the chip might be enough to oxidize the metal layers?
Hopefully they didn’t use flash cells to hold the ROM.
Man, just to say you are a god. I learn a lot from you, greetings from Brazil! ;o)
What in the name of Jerry Brightonhammer was that all about?
I dont’ know but it doesn’t make sense to me.
Nice. I absolutely agree with you.
Keep up the nice work. I’ll be back for more!
Oh I like that! Nice post.
This place is alright…I’ll be back for sure.