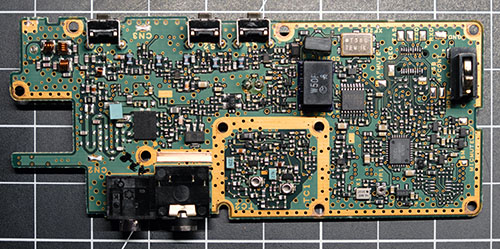
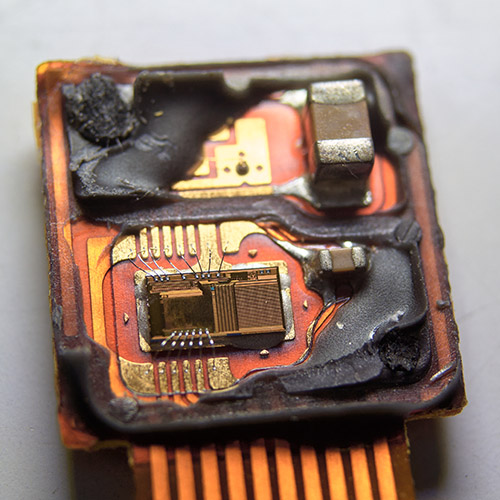
The Ware for October 2022 is shown below.
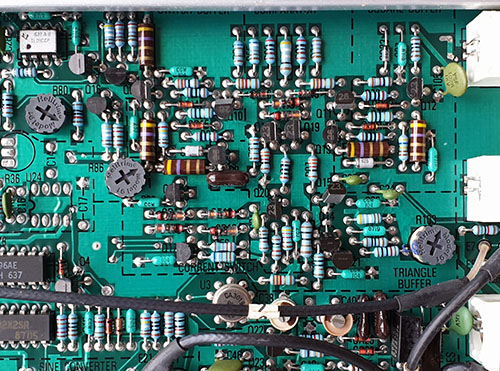
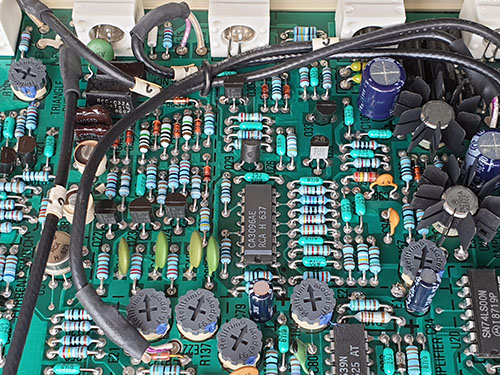
I think there should be ample clues in the first picture to guess the ware, but I included a couple of close-ups of the circuits because I love it when circuit boards document their functions so clearly. You can basically read the schematic directly off the traces. I also enjoy the motif of “here’s a ROM but no microprocessor” (the ROM is the ceramic-packaged 2716 in the top right of the first photo, with the label covering the UV erase window). ROM-based sequencers/FSMs and lookup tables were fairly common for this vintage, but these days most designs use ROMs exclusively to store code that is accessed by a CPU.